Last year’s Australian Cyber Security Centre (ACSC) Threat Report has been quite insightful in understanding the current IT security landscape. Incidences of data breaches and ransomware attacks have been steadily on the rise across a majority of industries, with many high profile data breaches reported last year, such as those from Uber, Equifax, Yahoo and Kaspersky Lab, to name a few.
Due to an alarming increase in such incidents, governments have enacted new compliance guidelines around data protection to safeguard businesses. As shared in our previous blog, the National Data Breach (NDB) scheme and General Data Protection Regulation (GDPR) are some of the new regulations this year that impose substantial fines on non-compliant businesses.
So what can you do to minimise the risk of becoming the next Cybercrime victim? How can you get started on a resilient cybersecurity strategy?
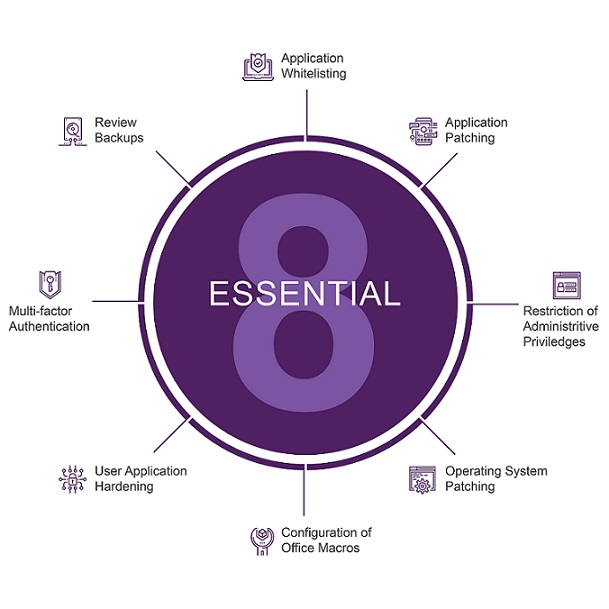
The Australian Signals Directorate (ASD), an intelligence agency with the Department of Defence, recommends below mentioned 8 strategies as a baseline to protect your business from the new age Cyberthreats:
#1 Application Whitelisting
Application Whitelisting is the process where you identify and allow only trusted and approved applications to run on your network or corporate devices. It is an extra layer of protection against rogue apps which may try to get into your network if an employee inadvertently clicks on a malicious link.
This strategy is likely to cause inconvenience to employees who may no longer be able to install their favourite personal app on the work machine, but it still might be worth putting up with little inconvenience than having to deal with a major security breach.
Quick Tip: If you are running Windows 10 or Windows Server (across all versions), it has a built-in whitelisting tool called AppLocker. AppLocker helps you control which apps or files users can run, which includes executable files, scripts, Windows Installer files, dynamic-link libraries (DLLs), packaged apps, and packaged app installers. You can find more information about AppLocker here.
#2 Application Patching
Despite being one of the oldest chores in the Infrastructure management space, this often gets overlooked by even the best of the support consultants. There is an inherent risk of functionality breakdown if patches are applied without understanding the impact and is a process which requires a test environment to avoid downtime. It can also be a tricky process when you have a large pool of applications to manage, in which case there are tools available to manage and automate the process.
Quick Tip: Microsoft System Center Configuration (SCCM) is a great tool for larger organisations that helps you to simplify the task of tracking and to automate the application of software updates in your Microsoft-based apps. You can read more information about software updates in SCCM here. There are third-party tools that can help you manage application patching beyond what SCCM can deliver, especially for small businesses where SCCM can be a little too overwhelming to maintain.
#3 Operating System Patching
Operating System patching is similar to Application patching, with a different area of focus that is equally important. You can also utilise SCCM to streamline your effort of managing OS patching.
Quick Tip: If your business is challenged with resources or skills to automate the patching process, we suggest you consider a Managed Services arrangement with an organisation like Professional Advantage with a team of skilled resources that leverages start of the art technology to handle this process efficiently and cost-effectively. This may also help your valuable internal resources focus on more mission-critical projects.
#4 Restriction of Administrative Privileges
There is a popular quote from the Spider Man series – 'With great powers comes great responsibility'. We believe It is easier to restrict the number of powerful resources, compared to making sure everyone you hand over the power is responsible and doesn’t misuse it. Admin privileges should be reviewed on a regular basis to ensure that only those that have the necessary permission have access to your sensitive data.
#5 Configuration of Office Macros
Too often, Macros from external sources come loaded with malicious content. The bad guys see this an easy way into the network as they can run automatically in Microsoft Office applications such as Word, Powerpoint or Excel. ASD recommends disabling the Macros unless there is a specific need to run them, in which case the sources should be verified and only trusted ones should be enabled.
Quick Tip: Please check this guide to understand how to manage Macros and if seems like a tedious task, we suggest you engage a Cybersecurity specialist to review Macro usage in your environment and make necessary changes to the policy and help manage them better.
#6 Application Hardening
Many cyber intrusions happen with ransomware and malware activated in Microsoft Office, Adobe- or Java-based apps, via web advertisements or even certain mobile apps. This is one of the reasons why application hardening is one of the crucial steps in risk mitigation recommended by ASD.
Application Hardening involves procedures that intend to remove security flaws from an app. It can be implemented by removing functionalities that you do not require. You can also restrict access to only the applicable users and keep it updated with patches. Before any security measure is adapted, however, make sure to test the impacts first to end users. The least you want to happen is to hamper productivity even when you’re securing your applications.
#7 Multi-Factor Authentication
A person owns an average of three devices—can be a combination of laptops, desktops, smartphones or tablets—as options to access their accounts. With the proliferation of these devices, many data breaches involve weak or stolen credentials. Multi-factor authentication (MFA) then becomes a good way to protect your account.
MFA utilises one of your physical devices to help confirm someone’s identity before they can log into their accounts. It typically comes in the form of authentication done through physical smart cards, biometric device, phone call and the most common, a randomly generated passcode.
Quick Tip: Microsoft has invested heavily in security. It has made a few of these security features available on the Office 365 Enterprise SKU for free and has made it easy to use for users and easy to manage for administrators. If you are an existing Office 365 subscriber, you can learn how to setup MFA here. You can also check out this page for various options on MFA with Microsoft Azure to suit your budget and needs.
#8 Review Backups
Backups ensure your business do not completely become immobilised when disaster strikes or in a ransomware or malware attack. While this is an important safety precaution in the event of security breaches or emergencies, sadly not many organisations regularly backup their data.
You can copy your files to a protected system and encrypt those that contain sensitive data. When doing backups, also make sure to test that your data is retrievable and accessible.
Quick Tip: Learn to backup your files on Windows 10 in this guide or you can opt for a cloud-based backup and recovery using Microsoft Azure. Of course, there are other third-party tools you can purchase and deploy for backup and recovery which you can learn to manage and use in no time. If your IT team, however, doesn’t have the bandwidth or the tools or skills to perform backup and recovery, you may also opt to sign up for a pre-emptive support services agreement with a reputable managed services provider. A dedicated support team will give you the peace of mind that someone keeps an eye on the safety of your data at all times.
Get expert guidance
Rolling out these eight essential strategies for risk mitigation isn’t a straightforward process when there are a number of things you need to consider and plan for. The tips we shared in this blog is intended to help you get started. To ensure a solid cybersecurity strategy using Essential Eight, however, you need a holistic view of your IT systems, intensive planning and multifaceted expertise. Fortunately, Essential Eight is one of the cybersecurity services that we can help you with.
Call us at 1800 126 499 for expert guidance on reviewing your IT security strategies or you can leave your comments below. If you think someone can benefit from our blog, share it on social by clicking the buttons below.