In our recent webinar, we emphasised the need for a shared language that bridges the gap between IT and business when discussing security. Often, IT teams speak technical when reporting to the board, leaving business leaders and the Board of Directors unsure about the real security posture and whether their business is truly protected.
To address this challenge and establish trust, a maturity framework plays a pivotal role in creating a common understanding of business risk and strategies to mitigate it. While numerous frameworks are available, each offering a unique perspective, all aim to provide IT and business managers with a shared vocabulary for assessing risk, security maturity, and progress.
In this blog, we touch on some of the more popular frameworks so you can consider the right one for your business, and how to keep track of your progress within Microsoft 365:
- Essential Eight.
- National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF).
- ISO 27001.
- Center For Internet Security (CIS).
Essential Eight
Essential security controls for Windows-based platforms.
Developed by the Australian Cyber Security Centre (ACSC), the Essential Eight is designed primarily for internet-connected Windows platforms. It represents the foundational cybersecurity controls that Australian organisations are strongly encouraged to implement. These eight essential controls aim to reduce the risk of cybersecurity attacks and mitigate the impact of successful attacks:
- Application Control: Preventing the execution of unapproved or malicious programs.
- Application Patching: Updating applications to fix known security vulnerabilities.
- Configuration of Office Macros: Blocking macros from the internet and only allowing vetted macros.
- User Application Hardening: Configuring web browsers to block malicious content.
- Restrict Administrative Privileges: Limiting the number of users with powerful access to systems.
- Operating Systems Patching: Updating operating systems to fix known security vulnerabilities.
- Multi-factor Authentication: Requiring more than one verification method for accessing sensitive information or systems.
- Regular Backups: Creating copies of important data and storing them securely.
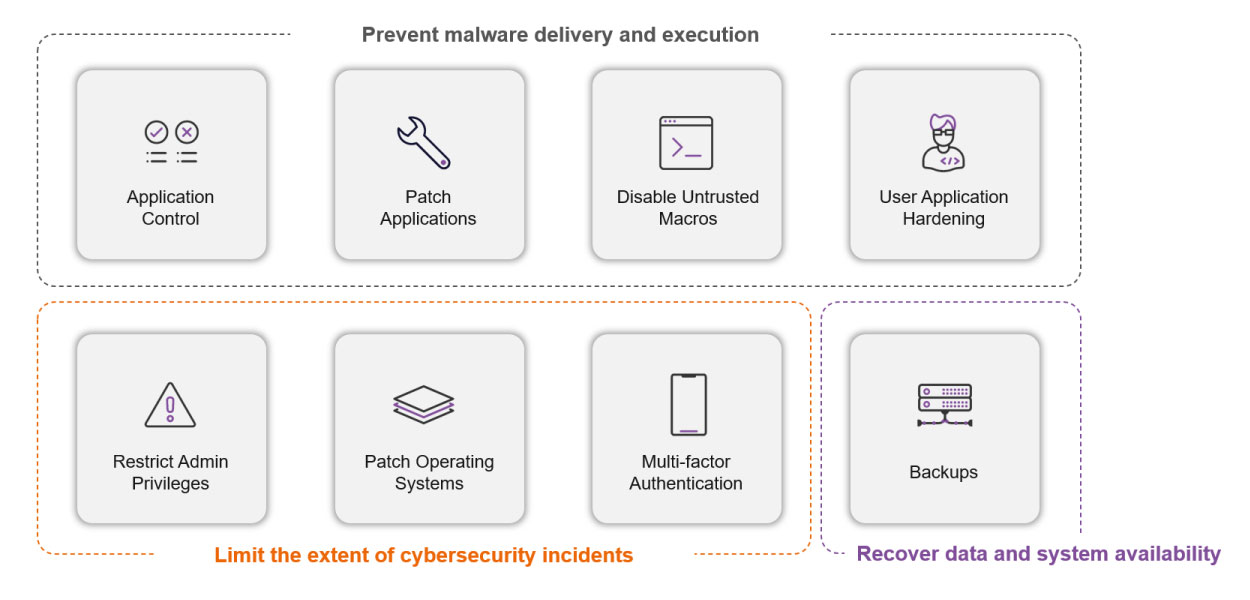
The eight essential controls are designed to achieve these three objectives.

Watch at your convenience: Essential Eight Cybersecurity from the Server Room to the Boardroom On-Demand Webinar
The Essential Eight Maturity Model offers a roadmap for implementing and evaluating the Essential Eight controls. It categorises each strategy into three maturity levels, ranging from basic to advanced. The ASD recommends that organisations attain consistent maturity levels across all eight strategies before progressing to higher levels.
While Essential Eight is not mandatory for most businesses it is highly recommended for Australian organisations. It is particularly relevant for organisations that must adhere to the Australian Government’s Information Security Manual (ISM) and the Protective Security Policy Framework (PSPF).
It’s also important to note that the Essential Eight is just the beginning. The ACSC has published a comprehensive set of strategies, totalling approximately 900 documented controls, alongside the Essential Eight. If you’re considering a starting point for a robust security framework, Essential Eight is a valuable consideration.
Cybersecurity Framework
Globally recognised cybersecurity recommendations for various platforms.
The NIST CSF, initially developed for US government entities, is a globally recognised and comprehensive set of cybersecurity best practices and recommendations. Unlike the Essential Eight, NIST CSF offers a broader spectrum of controls and extends its applicability to various platforms and organisations worldwide.
This framework is adaptable for organisations of any size, sector, or geographic region, providing a means to enhance cybersecurity posture while aligning with industry standards and best practices. NIST CSF revolves around five core functions: Identify, Protect, Detect, Respond, and Recover.
Furthermore, Microsoft cloud services have undergone rigorous independent audits and are certified in compliance with US FedRAMP standards, which are closely aligned with the controls outlined in the NIST CSF.
ISO 27001
A global standard for information security management.
ISO 27001 is an international standard for Information Security Management Systems (ISMS). It outlines the prerequisites for establishing an ISMS that guarantees the confidentiality, integrity, and availability of information assets. This standard also encompasses a comprehensive set of best practices, covering documentation, role assignments, access control, security measures, auditing, and both corrective and preventive actions.
Applicable to organisations of all sizes and across industries, ISO 27001 assists in identifying and evaluating information security risks. It facilitates the implementation of suitable risk-mitigation measures while continuously monitoring and enhancing ISMS performance. Moreover, ISO 27001 serves as a framework for achieving compliance with various other regulations and standards, including GDPR, PCI DSS, HIPAA, and more.
To demonstrate conformity with ISO 27001, an organisation can undergo a certification process by an accredited certification body. This involves an audit of the organisation’s ISMS against the standard's requirements. A successful audit results in a certificate that validates the organisation’s information security practices and provides assurance to its stakeholders.
Securing ISO 27001 certification is a rigorous process that can span from 6 to 18 months, contingent on your organisation’s complexity. Once achieved, certification remains valid for a three-year period.
Center For Internet Security (CIS)
Best practices for securing IT systems and data.
CIS is a not-for-profit organisation renowned for its globally recognised best practices in the field of IT systems and data security. CIS is primarily known for its pivotal contributions, which include the development of the CIS Controls and CIS Benchmarks, as well as the provision of specialised technology tools to empower security practitioners to implement and manage robust cyber defences.
Unlike the NIST CSF which offers a broader perspective on cybersecurity, the CIS controls are notably more specific. Designed with cross-compatibility in mind, they are intentionally crafted to align seamlessly with various cybersecurity standards, such as PCI DSS, GDPR, HIPAA, and ISO 270011. This design approach ensures organisations can navigate the complex landscape of cybersecurity requirements without running into conflicts or compliance challenges.
The extensive suite of CIS Benchmarks comprises comprehensive configuration recommendations spanning 25+ vendor product families. These encompass widely used platforms like Microsoft 365, Microsoft Azure, Microsoft Dynamics, Amazon, Oracle, Google, VMWare, Zoom, and more. These benchmarks represent the collaborative efforts of cybersecurity experts worldwide, offering prescriptive guidance that enables organisations to fortify their systems against evolving cyber threats confidently.
Which cybersecurity framework is right for your business?
Selecting the appropriate cybersecurity framework for your organisation hinges on several factors. These factors include your organisation's size, industry, regulatory requirements, existing security posture, and specific cybersecurity objectives. Each framework discussed in this blog possesses its own unique strengths and areas of focus. Therefore, it's crucial to tailor your choice to your organisation's distinct requirements and circumstances.
As you contemplate which framework to adopt, consider the following:
- Business objectives. Begin with a clear understanding of your cybersecurity objectives. Are you aiming to satisfy specific regulatory mandates, bolster overall security, or enhance incident response capabilities?
- Regulatory compliance. Assess whether your industry imposes particular cybersecurity regulations or standards that demand adherence. Some frameworks are better suited to addressing specific regulatory requirements.
- Resources. Evaluate your organisation's available resources, including budget, staff expertise, and available tools. Different frameworks may necessitate varying levels of resources for implementation and maintenance.
- Risk profile. Understand your organisation's risk profile and the types of threats it faces. Certain frameworks may provide more guidance on tackling specific threats or vulnerabilities.
- Scalability: Consider whether the framework can seamlessly grow and adapt alongside your organisation’s evolving needs.
- Industry best practices: Explore industry best practices and standards relevant to your sector. Certain industries feature cybersecurity frameworks or guidelines tailored to their specific needs.
- Alignment with existing practices: Evaluate how well each framework aligns with your current security practices and whether it complements or overlaps with your existing efforts.
- Certification and validation: If certification holds significance for your organisation, explore frameworks like ISO 27001 that offer certification options.
Can I use Microsoft Secure and Compliance Score to track my compliance with any of these frameworks?
Microsoft Secure Score and Compliance Score serve as powerful central administrator tools, providing valuable insights into the status and progress of various frameworks. They facilitate streamlined reporting to both your business stakeholders and auditors.
As an integral component of the Microsoft Purview Compliance Manager, the Purview Compliance Portal is a valuable resource for comprehending your organisation's compliance posture and implementing risk mitigation measures. Within Compliance Manager, you'll find premium templates designed to facilitate assessments for a wide range of frameworks, including those mentioned above, such as IRAP, APRA CPS, various ISO standards, and more.
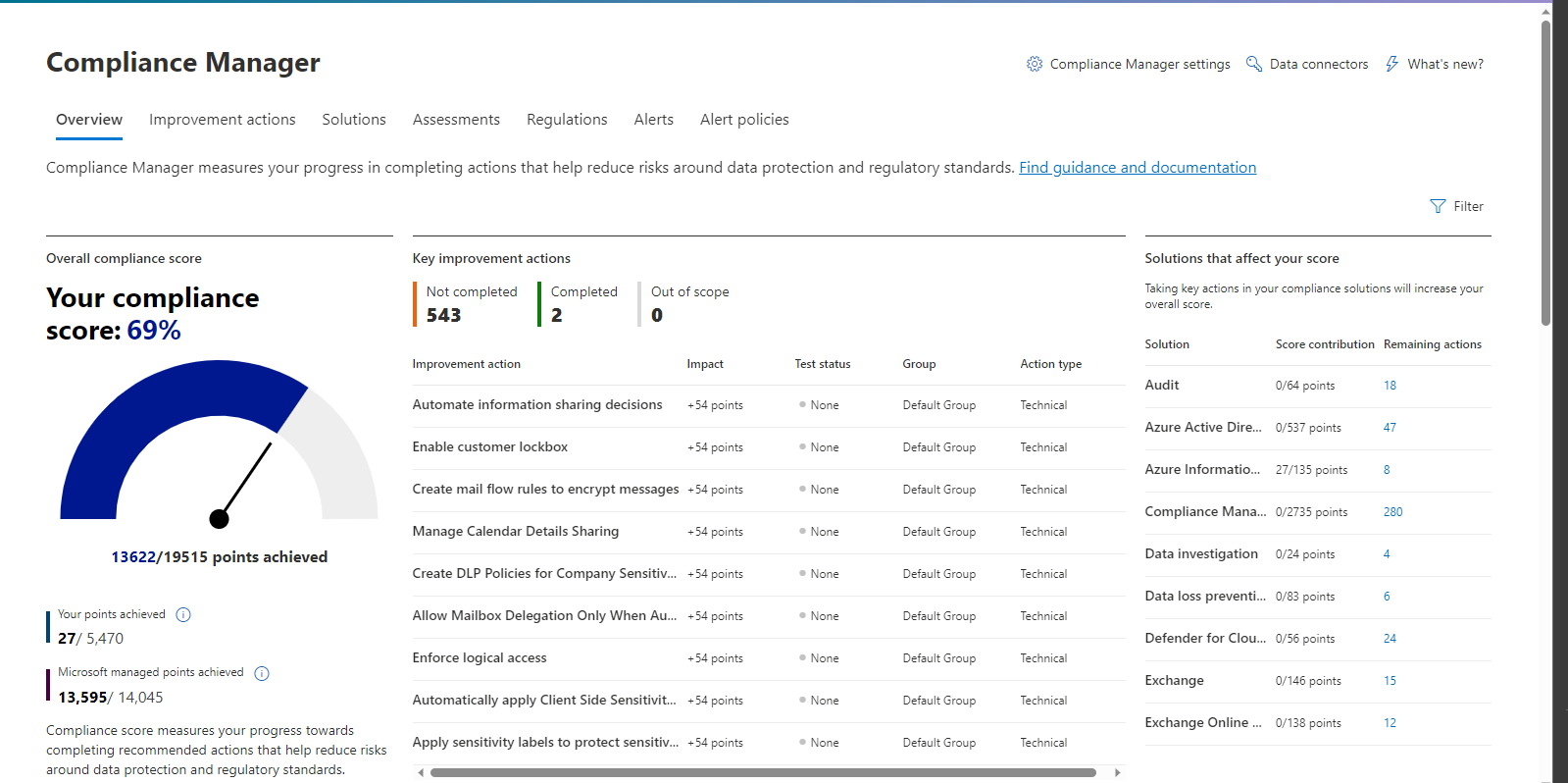
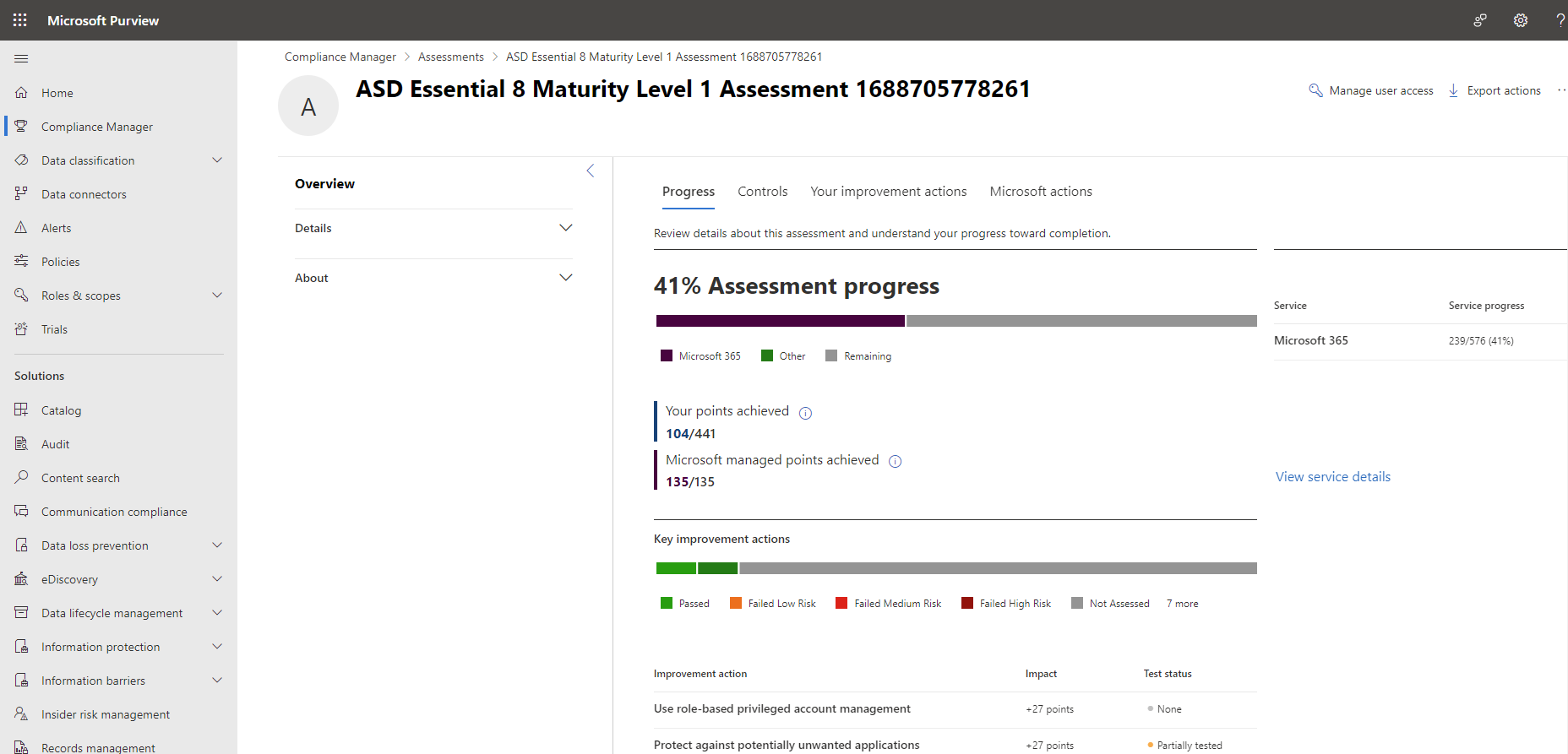
If you need assistance understanding what’s required for aligning to the above frameworks or deploying the controls required for these frameworks, Professional Advantage can help you with a Cybersecurity Maturity Assessment and provide you with an action plan to help you achieve your intended goals.