The majority of security breaches we have heard of recently were triggered by unpredictable behaviour of any organisation’s greatest asset – their Employees. Whilst the security veterans are working tirelessly to come up with strategies to mitigate these risks, do you know what typical employee behaviours generally lead to these incidents?
Here we list some of the common scenarios so you can start arresting the behaviour before it leads to a security issue.
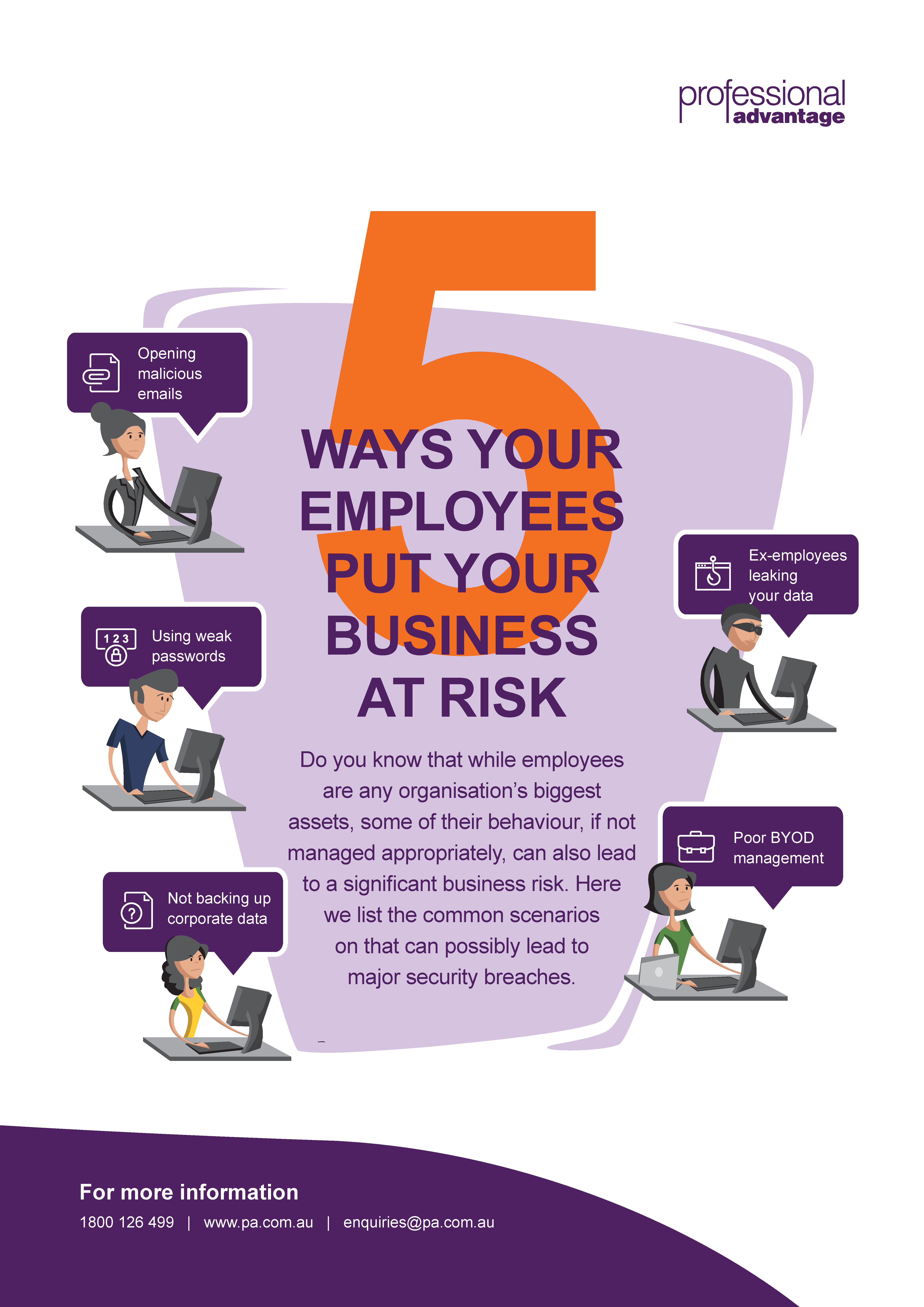 DOWNLOAD INFOGRAPHIC – 5 ways your employees put your business at risk.
DOWNLOAD INFOGRAPHIC – 5 ways your employees put your business at risk.
1 Opening malicious emails
It is very common to receive a spear phishing email in your inbox with a link to something you have won, view a photo, download a video, etc. To make things harder, lots of times the sender pretends to be a well-known brand such as a major bank, major retail chain, an airline, etc. These emails are mainly trying to infect your system with a keylogger to capture your login credentials, which are then used as a gateway to other parts of your work network or trick your business partners to initiate fraudulent payments to attacker’s bank accounts.
As cybercriminals have become more advanced and creative with carrying on these attacks, phishing has also become a lot harder to be detected by an untrained eye. Apart from educating your people, there are some other recommendations to keep these cyber threats at bay. One of them is Application Whitelisting where you identify a list of trusted and approved applications that can run on your network. Once it is enabled, despite clicking a malicious link, something like a keylogger wouldn’t run on the staff’s PC and can potentially save you a major security breach.
2 Weak passwords
Most employees are probably guilty of this and some even make it worse by keeping it the same password for a very long period of time. It is similar to building a strong castle with high walls, watch towers, retracting bridges, deep moats, strong bars across the windows, and having a cheap lock in the front which can easily be exploited by the bad guys to bypass every other security piece you have installed. Weak passwords like birthdays or consecutive numbers like 123456 are very easy to guess.
Educate your employees about the importance of keeping their passwords safe and using complex ones that are hard to guess. Implement policies that enforce having passwords that combine numbers, special characters and different letter cases. You can even include in your policy having to change passwords every 45 to 90 days and not allowing them to reuse previously used passwords. It may annoy some users, but will surely work for the business.
3 Not backing up corporate data
We often hear these days that your Data is your Dollar value. In this day and age, talking about the importance of backing up data may look redundant, because most businesses do it anyways. The challenge most businesses face is that some users don’t clearly understand what locations are being backed up and end up saving valuable content on locations such as desktops, personal drives which are often not part of the backup regime. In case there was a security breach encrypting any of these non-backed up locations, it could mean a reasonable financial loss to the business due to data loss.
You can reduce the impact of a cyber intrusion by educating your staff on storage locations that get backed up, which will then help you recover quickly from an incident. Existing Office 365 subscribers have the option to back up their files in the Cloud using OneDrive for Business or use the more advanced means through Microsoft Azure. You can read more about Azure backups here.
4 Poor BYOD (Bring your own device) management
It is not uncommon for employers to enable BYOD programs to keep up with the increasing demand for flexible working. Whilst these programs offer greater flexibility to the new generation of workers, they do add another level of complexity for IT to secure corporate data. BYOD is a great business model, which comes with its fair share of business risks such as data leakage, limited control over device security which could mean serious security holes that can be exploited by hackers. A commonly known threat to personal devices is malware that is installed inadvertently by the user, which can potentially find its way to the corporate network.
Microsoft has heavily invested in technologies that help you find the right balance between productivity and security. Office 365 subscribers can utilise BitLocker to encrypt Windows devices or turn on Data Loss Prevention (DLP) and Information Rights Management (IRM) for better protection of your sensitive data.
For more advanced threat protection, there’s Microsoft Enterprise Mobility + Security (EMS), a device-management and virtual-identity management suite that provides you all the tools you need to administer, provision and secure the devices that you use in your organisation. You can read more about EMS here.
5 Ex-employees leaking data
Disgruntled ex-employees can often do more harm to the business than what you would expect. Simply disabling their user accounts after letting them go, may not be sufficient these days. They may still try to access your company data through a friend and perhaps a sympathetic former colleague so it is important that you understand where your sensitive data resides and what attention is required to ensure it is a safe event from rogue insiders.
Fix their bad habits
How do you address these habits that put your business at risk? You can begin by building a cyber safe culture starting off with the senior leadership team. Without management support, the chances of employees getting onboard your security initiatives are likely to be an uphill battle. Follow it through with delivering regular communication and learning sessions to help them better understand risks and the roles they play in protecting the business from cyber threats.
Do you have the right IT security strategies in place?
As employees will always play a role in your overall security, in addition to user education, you should also focus on building a long-term security-focused IT strategy. The Australian Signals Directorate (ASD), an intelligence agency within the Department of Defence recommends below mentioned Essential Eight Strategies as a baseline:
- Application Whitelisting
- Application Patching
- Operating System Patching
- Restriction of Administrative Privileges
- Configuration of Office Macros
- User Application Hardening
- Multi-factor Authentication
- Review Backups
Implementing ASD’s Essential Eight will significantly reduce the risk adversaries trying to compromise your business systems. Furthermore, implementing the Essential Eight proactively can be more cost-effective in terms of time, money and effort than having to respond to a successful large-scale cybersecurity incident.
If you are not confident about your existing cybersecurity strategy, Professional Advantage can assist. We provide Essential Eight Strategies, risk assessments as well as network and vulnerability scan services, all of which you can find here if you would like to know more information about it. You can also talk to us at 1800 126 499 or you can leave your comments below if you have questions.