Compliance is one of the major concerns for most businesses we speak to and with the ever changing IT landscape, it is becoming increasingly hard for organisations to enhance staff productivity while staying compliant. This year we saw two major regulations come into play, to protect personally identifiable information (PII). Whilst these regulations are aimed in the best interest of community at large, they have posed a significant challenge for businesses to be compliant.
The National Data Breach (NDB) scheme and the General Data Protection Regulation (GDPR) both impose massive fines for non-compliance in case of a data breach, as explained in our previous blog post. Analysts estimate that the cost for non-compliance is up to three times the cost of being compliant.
Are you an Office 365 subscriber?
Did you know that Microsoft Office 365 can be instrumental in your compliance process? It is designed to conform with industry-leading security measures and compliance policies including GDPR and can help you manage the security of your data at rest or in transit, in many ways. See below listed a few:
-
Manage compliance activities
There is often a disconnect between the compliance personnel who understand the business requirements and IT professionals who are more across possibilities from a technology standpoint. To bridge the gap and accelerate the assessment process, Microsoft offers Compliance Manager as part of your Office 365 subscription to get things started. It is a workflow-based risk assessment tool to assist you to track, assign and verify your organisation’s regulatory compliance activities.
-
Understand your security position
As part of your compliance journey, Secure Score can be a very helpful tool to beef up your security levels. It automatically figures out what Office 365 services you are currently using and then compares your settings to the base line configuration recommended by Microsoft. It also provides a list of action items to help you get most out of the built-in features, which then improves your overall score.
-
Encryption of physical disks
Until recently, businesses weren’t too sure about data security in the Cloud as they didn’t think it could match the level of security of their on-premises infrastrucuture could offer. The scenario has changed recently as with the changing security landscape, the level of protection backed into SaaS offerings by major players such as Microsoft, is unmatchable.
One of the key features that is extremely valuable from regulator’s perspective is encryption. It ensures that the data is not intelligibly readable even if it is accessed by unauthorised users. Microsoft utilises multiple layers of encryption to provide enterprise grade security to protect your valuable corporate data against new age cyber threats. One of the key encryption technologies that protects your data while at rest in the data centres is BitLocker. It reduces the risk of data leakage through unauthorised physical access to the disks or hardware recycling.
-
Encrypt data at the application level
Microsoft also provides another layer of protection at the application level through Service Encryption. This ensure files and mailboxes within Exchange Online, OneDrive for Business and SharePoint Online are encrypted. With Service Encryption, even if someone gets through the physical security barrier, they won’t be able to get to the data since it is further encrypted at the application layer.
-
Encrypt emails and files in transit
In addition to TLS encryption commonly used to secure mail data in transit, Office 365 offers another level of item level encryption that is more granular, through Office 365 Message Encryption and Azure Information Protection. These features make it easy to protect confidential business information based on specific keywords. You can implement rules to identify keywords in the email body, subject headline and then create relevant labels to restrict message recipients from forwarding, copying, editing or printing your message. Documents and emails protected by Azure Information Protection stay protected regardless of their location, whether it’s within the corporate network or external. That means even if the content ends up in someone’s personal email account such as Gmail or Hotmail, it stays encrypted.
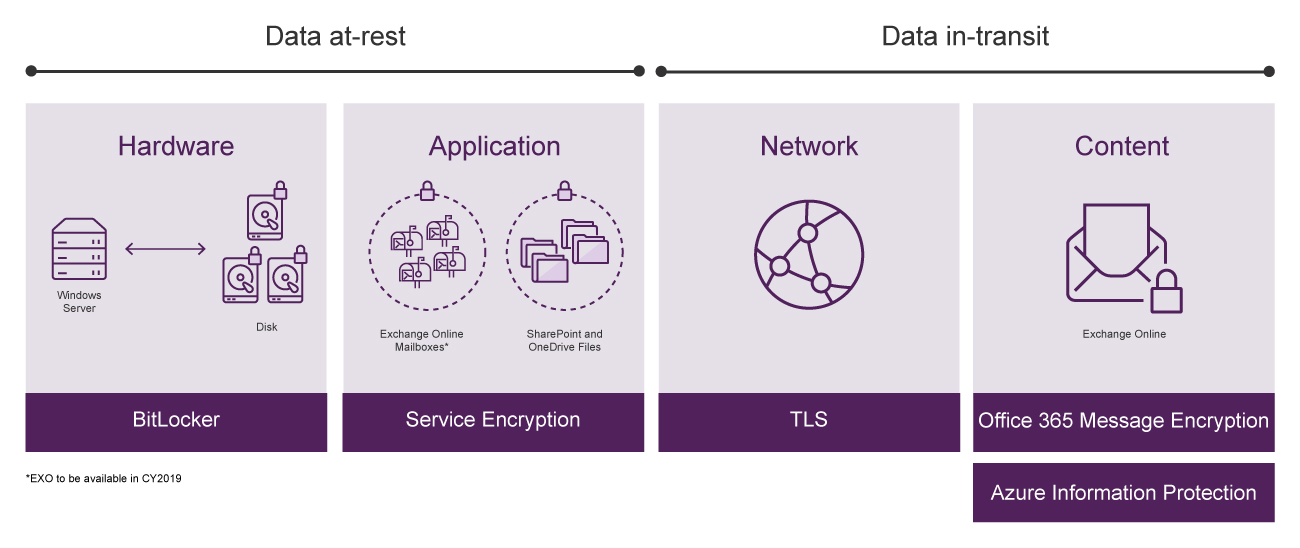
Source: Microsoft Inspire 2018 presentation
-
Monitor and track user activities
Audit logs can be key in figuring out root cause of a security incident. In case any valuable content is maliciously deleted, moved or copied, you can find out who has done that and then investigate the intention. Office 365 enables you to monitor and track user and administrator activities through the Office 365 audit logs. All user requests, approvals and any actions done are logged and available for audit which can be used as documentary evidence to meet compliance requirements.
-
Control how Microsoft accesses your data
Not having access to the physical hardware in Office 365 does concern some businesses with the fear of not knowing who else will have access to the corporate date. To address such concerns and maximise data security and privacy, Office 365 subscription includes an option to enable Customer Lockbox. This ensures Microsoft engineers don’t have standing access to your data and require explicit approval from a designated user before the data is touched, even for maintenance purposes. More information about how Microsoft manages your data here.
-
Allow 'just in time' access for high privileged roles
Most organisations use the traditional ‘standing access’ for global administrators, which can often be a security risk as the user then becomes a permanent admin who only needs to perform a small operational task occasionally. The Australian Signals Directorate has even listed ‘Restricting Administrative Privileges’ as part of their Essential Eight risk mitigation strategies recommended for every Australian business. To help you address the risk, Microsoft has introduced a new role of ‘Eligible Admin’ for the users who need privileged access every now and then. The Privileged Identity Management (PIM) in Azure AD and Privileged Access Management (PAM) in Office 365 allows you to manage and control access better within your organisation through the ability to offer ‘just in time’ and ‘just enough’ access.
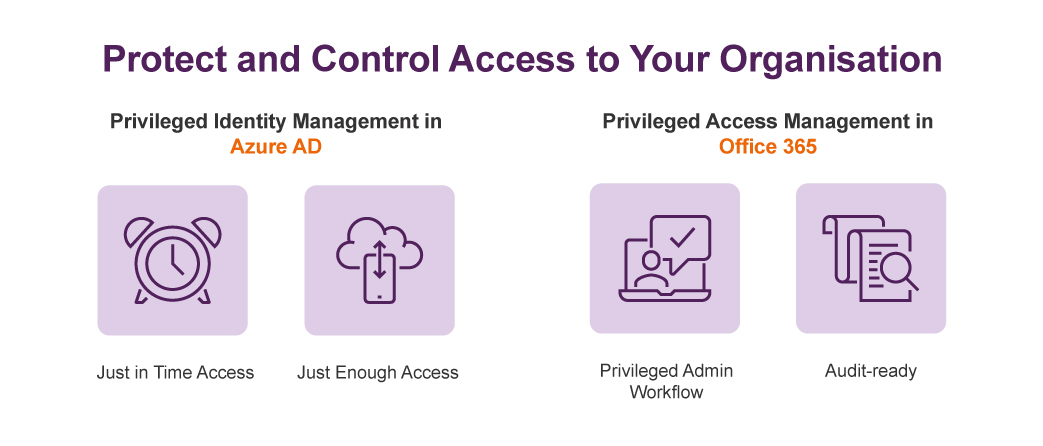
Source: Microsoft 2018 Inspire presentation
Become compliant with Office 365
Knowing where your data resides and the ability to control your valuable data are key for your organisation to be fully compliant with the new regulations. All of the encryption, access control and threat detection capabilities in Office 365 are available to you to help you identify and manage access to personal data. These capabilities are auditable which you can potentially use as evidence in case a security breach. While Office 365 alone does not enable you to become 100% compliant with GDPR or NDB, it can certainly help your compliance journey to be a lot easier.
Have questions about Office 365 security? Call us at 1800 126 499 or leave your comments below.